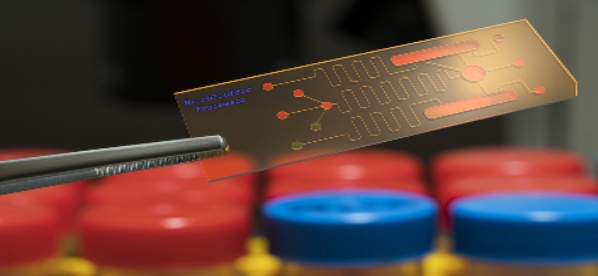
A biochip is a bio-microarray device that has been extensively developed and studied for enabling a large -scale analysis of genetics and proteomic and functional genomic experiments.
They refer to a set of diminished microarrays which are placed on a substrate. This substrate allows various experiments to be executed at the same time. Biochips are devices that contains millions of sensors and sensor elements.
The greatest advantage of DNA arrays is its high speed, throughput and the fact that they are useful in various genomic applications such as nucleotide polymorphism analysis (SNP), disease classification, gene expression studies, prediction of function, development of new drugs, clinical diagnosis, toxicological studies etc.
Like other methods of detection which are molecular – based, such as PCR (Polymerase Chain Reaction), microarrays also target genes which are specific to pathogens for detection. They allow large – scale screening of multiple targets because of their high speed and throughput power.
Digital biochips have become one of the most powerful and promising technologies in many fields of biomedicine. In a digital biochip, a group of cells which are adjacent to each other in a microfluidic array can be configured in order to work as storage and functional operations as well as for transporting fluid droplets in a dynamic form.
These biochips are not same as microchips. Microchips are electronic devices, but biochips are not electronic. These biochips can be considered as a microreactor which can detect enzymes, proteins, DNA and antibodies.
The primary function of biochips is performing many biological reactions in less time.
The steps of working of biochips are:
- A low power electromagnetic field is generated through radio signals by the operator.
- The biochip turns on. The fixed biochip gets turn on
- The identification code is transmitted by the activated chip. It is transmitted reverse to the operator by radio signals
- The received code is strengthened by the reader in order to change it into a digital form and finally to exhibit it on LCD.
Biochips have two components:
1)TRANSPONDER: Transponder can be of two types which are active and passive transponder. Passive transponders have no charge on its own whereas active transponders have charge when the operator activates it by giving a low electrical charge. Transponders have 4 parts which are antenna coil, glass capsule, tuning capacitor and computer chip.
2)READER: The reader consists a coil called an “exciter”. Through radio signals, this coil forms an electromagnetic field. It provides the energy that is needed to activate the biochip. The receiving coil is carried by the reader in order to receive the ID number or the code which was transmitted and was sent back from the excited or activated biochip.
TYPES OF BIOCHIPS:
There are 3 types of biochips:
- DNA Microarray:
DNA microarray is a set of small spots of DNA that are fixed to a strong surface.
- Microfluidic Chip:
These are a choice to usual biochemical labs and are transforming several applications like DNA analysis, proteomics and molecular biology procedures which are known as the study of proteins and diseases that are diagnosable.
- Protein microarray:
The method of protein microarray is used for following the actions as well as the connections between proteins. Along with this they are used to find out the functions of the proteins on a large scale. The main advantage of these chips is the fact that a large number of proteins can be tracked parallelly.
.
ADVANTAGES OF BIOCHIPS:
1)They are small in size, faster and powerful.
2)Bio chips can be used for identifying people individually.
3)Bio chips are useful in finding people who are lost.
4)Bio chips have the ability for performing several thousands of reactions in a few seconds.
DISADVANTAGES OF BIOCHIPS:
1)Bio chips are very expensive.
2)They can raise problems of individual privacy.
3)These chips can be fixed into human bodies without any interference from them.
4)There is a chance of turning every individual into a controlled individual.
APPLICATIONS OF BIOCHIPS:
There are a wide range of applications using biochips:
1)A bio chip leads to e-commerce systems that are safe.
2)These chips can be used for locating or tracing a person or animal anywhere in the world.
3)Biochips are very effective in restoring the records related to cash, passports, medical files etc.
5)They are used for storing and updating the information of a person such as demographics, financials, medical etc.
6)They can be used in the medical field in the form of BP sensors, oxygen sensors, glucose detectors etc.